How to access the deep web
Although the information on the deep web is not indexed by common search engines, it can still be accessed. Accessing deep web content is generally safe, and a common practice for many internet users, such as logging into Gmail or LinkedIn, or accessing the Wall Street Journal.
However, deep web user accounts often contain personal information that could be valuable to criminals, which is why access to much of the deep web is restricted.
The deep web, including the dark web, does not come to users. Spam and phishing attacks may originate from a dark web marketplace, but a user must download something infected from that marketplace to release malware. The dark web site itself does not initiate the attack.
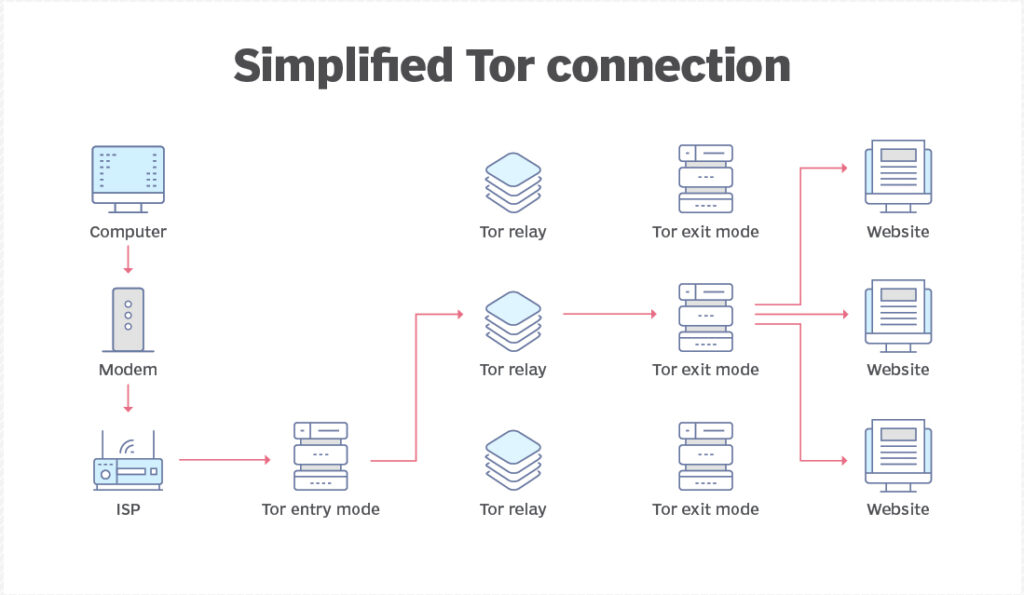
Access to the dark web is intentionally hidden and requires specific technologies, such as the Tor browser or the Invisible Internet Project (I2P) network. Both tools have legitimate purposes, such as protecting a user’s IP when visiting websites or helping journalists report from hazardous locations through the use of the I2P network as a proxy.
Access to a dark web marketplace requires the use of the Tor browser. Although it is based on the Mozilla Firefox browser, Tor is not maintained as well and can have difficulties rendering pages.
However, there is a valid reason to explore the dark web. Given the discussions of hacking and exploit trading, it can provide insight into emerging, unknown vulnerabilities. Monitoring the dark web can give users a head start in knowing about exploits before they become widespread threats.
Leave a Comment